A. What is Authentication?
Authentication is a process of verifying someone’s identity (i.e. identity checking). For example, when you want to login to a website, you might need to provide your username and password. The website will check your username and password to ensure that “you are who you claim to be”.
The website will check if the username and password you provided is correct. If it is correct, then you will be granted access to the website. Otherwise, you will be denied access (code: 401 Unauthorized).
Important: authentication doesn’t apply only to the user. It could also apply to other cases, such as when your browser wants to access a 3rd party service, or when your application servers wants to communicate each other.
B. What is Authorization?
Authorization is a process of verifying someone’s permissions (i.e. access control checking). For example, you are logged in in to a website already (i.e. authenticated), and you want to perform an action (e.g. create a new post), the application are going to check if you are allowed to perform this action or not. If you are not allowed to perform this action, the application will deny your access (code: 403 Forbidden).
C. Authentication Strategies
There are several authentication strategies, such as:
- Basic Authentication
- Session Based Authentication
- Token Based Authentication
- JWT Authentication
- OAuth
- Single Sign On (SSO)
C.1. Basic Authentication
This is the most basic authentication strategy. It is simple and easy to implement, but it is not secure. It is also not suitable for large-scale applications.
By the way, this method is not equal to username-password authentication.
Basic Authentication is the part of HTTP specification and the details can be found in the RFC 7617. Here is the steps:
- Browser tries to access a protected URL (e.g.
/users). - Server does not find the
Authorizationheader. - Server sends the response back to the browser:
- Status Code: 401
- Header:
WWW-Authenticate: Basic realm="users_page"
- Browser shows the login form (username & password).
- Browser submits the form with the following headers:
Authorization: Basic <base64(username:password)>
- Server decodes the base64 to get the username and password.
- Server verifies the username and password.
- Server sends the success response (status code: 200) back to the browser.
C.2. Session Based Authentication
In this strategy, a small user data (i.e. session) will be generated in the server when the user logs in. This session will later be utilized by the server to identify if the user is logged in or not.
Session is a small user data, stored as simple object. It may contain a user information such as user id, name, email, etc. Session will be stored in memory (could be directly in the server itself or 3rd party tools such as Redis) or even in the database.
C.2.1. Login Flow
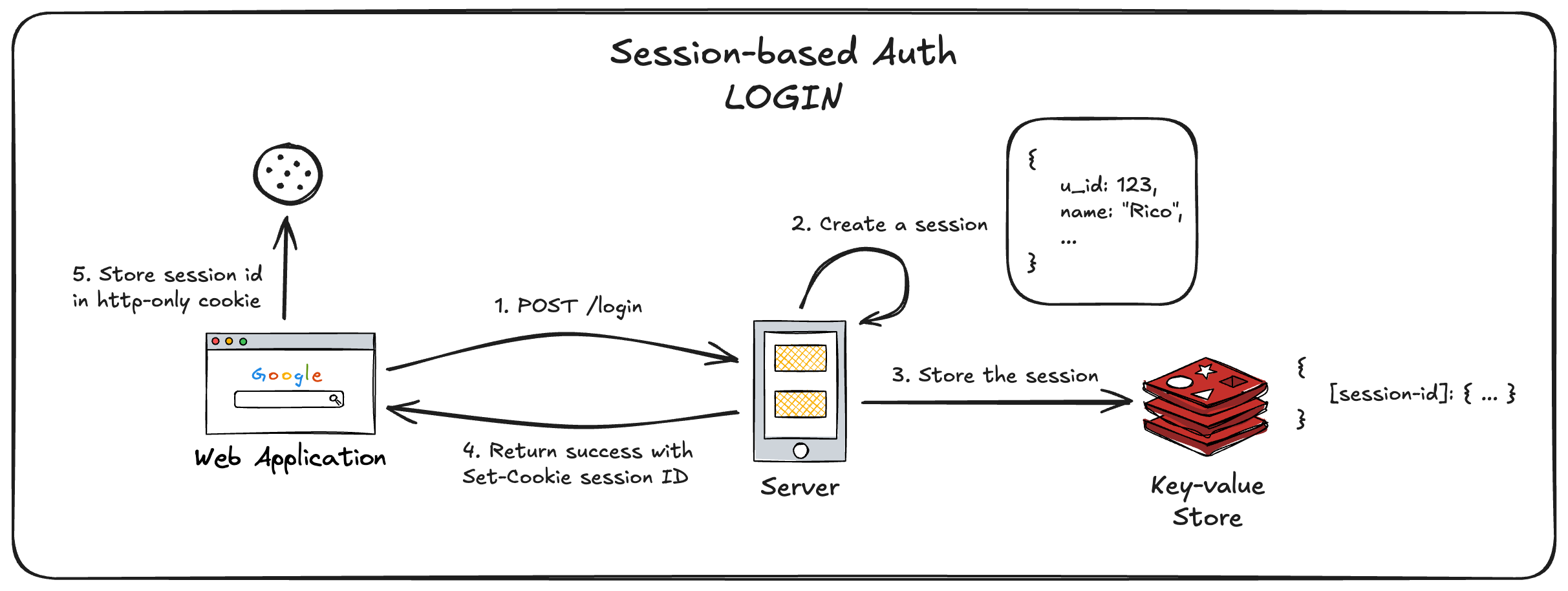
- User enter the email and password in the login form and submits it.
- Browser sends the request to the server.
- Server verifies the email and password.
- Server generates a session for the user.
- Server stores the session in memory.
- Server sends the success response (status code: 200) back to the browser with set-cookie header containing the session ID - unique identifier for accessing the user session data.
- Browser stores the session ID in the cookie.
C.2.2. Data Access Flow (success case)
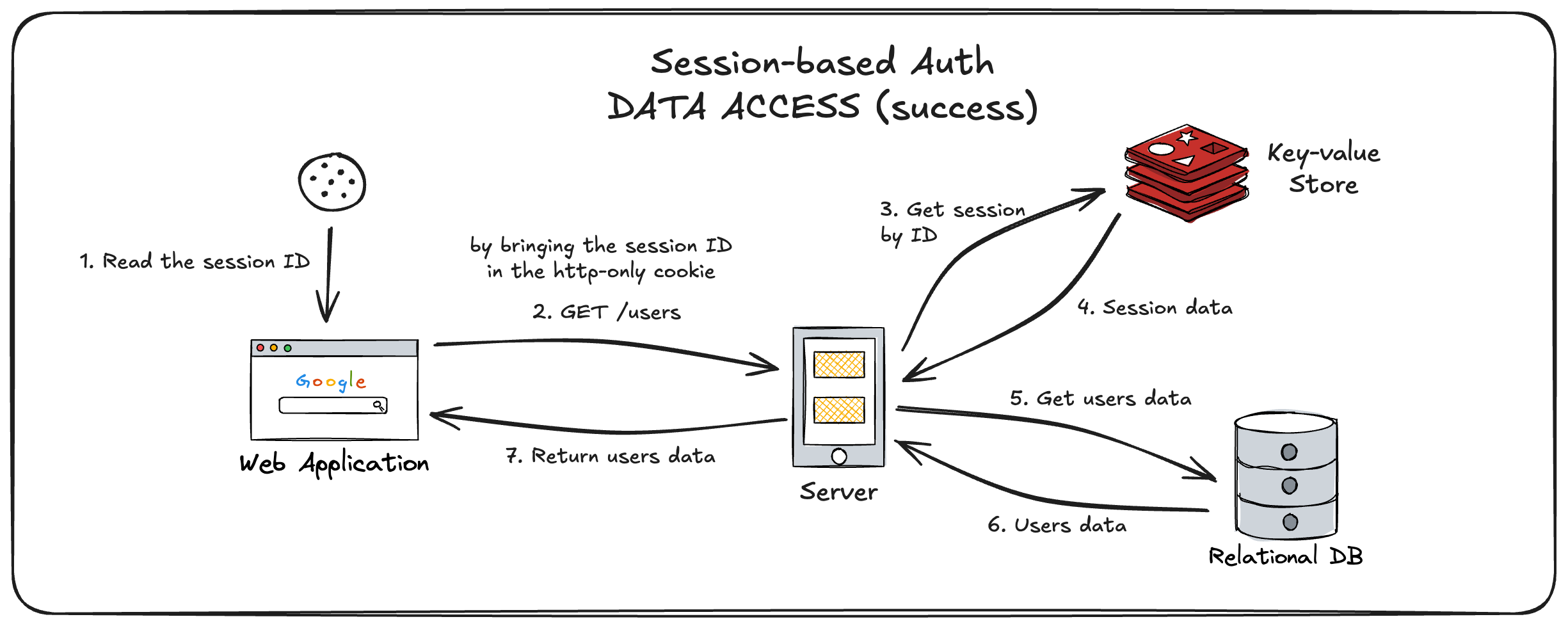
- User opens the a protected page.
- Browser sends the request to the server to get the necessary data.
- Server verifies the session based on the session ID attached in the cookie.
- Server retrieves the requested data from database.
- Server sends the success response (status code: 200) back to the browser as well as the data.
C.2.3. Data Access Flow (failure case)
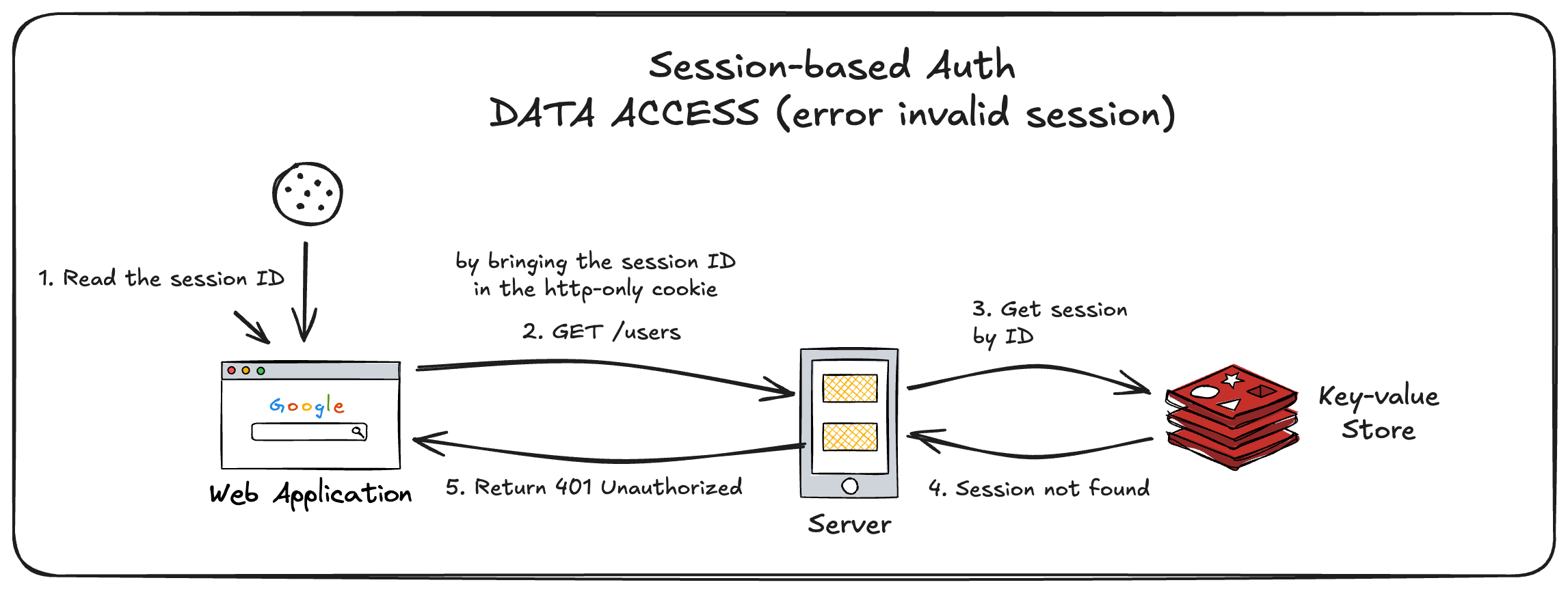
- User opens the a protected page.
- Browser sends the request to the server to get the necessary data.
- Server verifies the session based on the session ID attached in the cookie.
- Failed due to expired session or invalid/missing session ID.
- Server sends the error response (status code:
401 Unauthorized) back to the browser.
- Server sends the error response (status code:
- Failed due to not allowed to access the data.
- Server sends the error response (status code:
403 Forbidden) back to the browser.
- Server sends the error response (status code:
- Failed due to expired session or invalid/missing session ID.
C.3. Token Based Authentication
TODO
C.4. JWT
TODO
C.5. OAuth
TODO
C.6. Single Sign On (SSO)
TODO